Guardzilla All-In-One Video Security System Review
Guardzilla – Set Up
I had a fair amount of trouble with the setup which appeared so effortless in the video overview. I consider myself pretty savvy and while not the networking guru like our west coast writer Ken Brown, I have a better grasp of the technology than the average Joe (no pun intended). As I outline below, I had some connectivity issues but if you read through my ramble, you’ll see that I finally did resolve this.
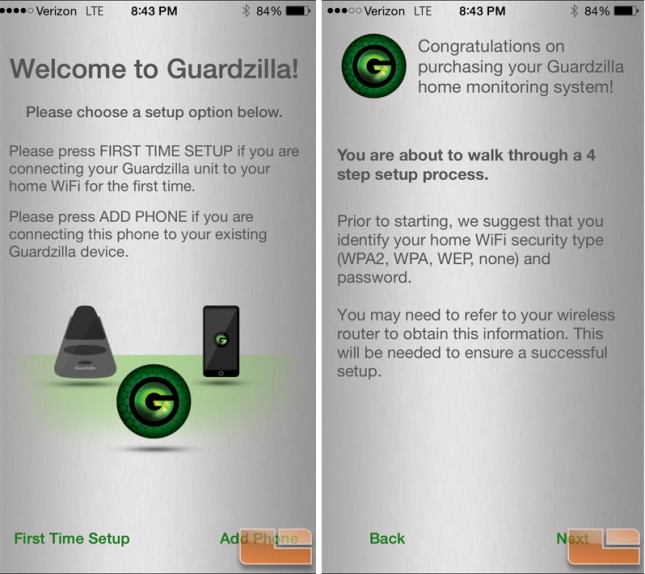
Kicking things off in the setup, Guardzilla broadcasts its own Wi-Fi signal so that you can connect directly to it using their free app on Android or iOS – the latter of which is what I used. The wizard actually does a pretty good job and is designed simple enough for those that are less tech savvy to be able to complete the setup without calling someone for tech help. That is, until you run into issues connecting as the literature available for troubleshooting is sparse.
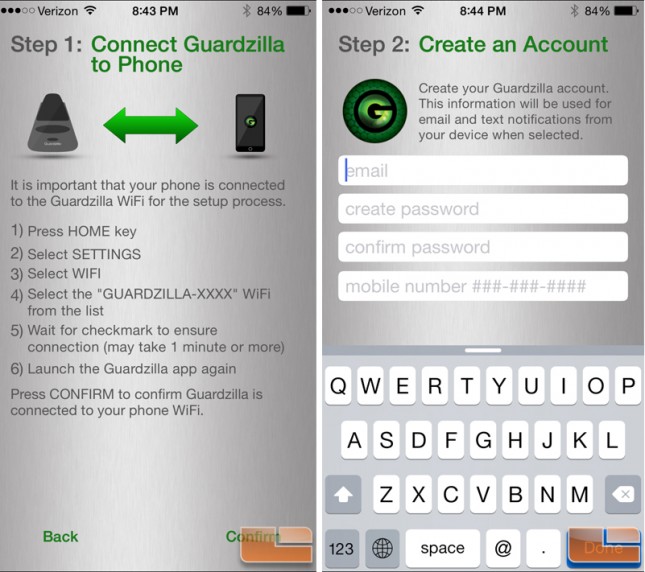
My iPhone 6+ had no problems seeing the Guardzilla network and connecting although they weren’t exaggerating when they say it may take a minute or two to connect. Once connected, I entered the information needed to create an account. It’s at this point where I’m going to point out one of my biggest complaints the product documentation. Being inquisitive, I begin asking myself where this “account” data is stored, whether on the device, in the app or in the cloud? I received no email confirmation that an account was created or to validate the email address which makes me think that it is local to the device or the app. How do I update the email or the associated phone number? This is a problem. What if my email or phone number changes? These aren’t rare occurrences. What if I sell the device? Resetting (via the button) does not trigger a fresh account setup scenario. I know this because I used it quite liberally in the next step. Once again, this is not part of any of the documentation, help topics, etc that I could find which is a huge oversight on Guardzilla’s part in my opinion. Finally, after my testing concluded I deleted the app to see if I would have to go through the initial setup all over again once the app (but not data) was restored. Lo and behold I did have to re-do the setup and was able to alter the account information had I wanted to. This is probably the best design for storing the data so it is never transferred with the device and cannot be stolen off of could servers. However, it really should be an option in the app to edit this data or at the very least addressed in the documentation.
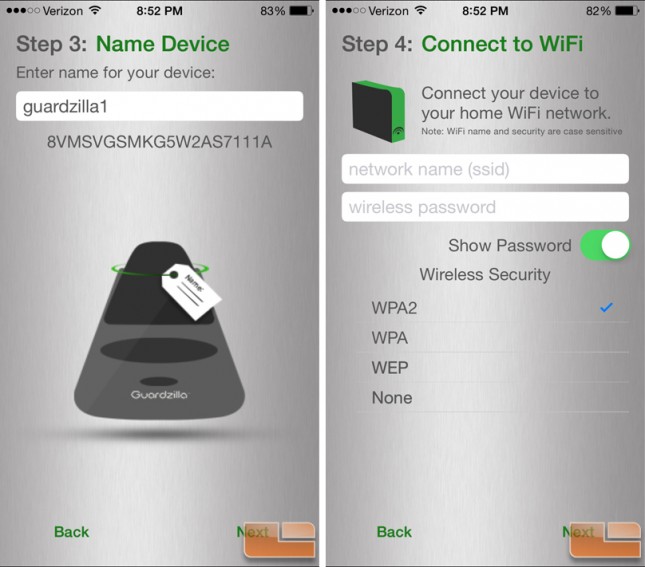
The next step is to give the device a unique and/or intelligent name based on it’s location which can be handy if you have more than one. I decided to go generic and slap the number 1 at the end of the “Guardzilla”. Hooray for simplicity. Now is where I give Guardzilla the specifics of the network to which it should connect. Simple, right? On the iPhone (not so for Android per the documentation), the app will not detect any available networks but instead you have to manually enter in the SSID, password, and specify the security protocols, if any. The exercise itself is simple but the results were disappointing. I tried multiple times to connect to my WPA2 secured network broadcast on my ASUS RT-AC68U router. After several attempts, the device would no longer be seen by the app and I would have to reset it with the reset button held in for five seconds. I tried a handful of times with the same result. I have a host of home automation products hooked to my network such as a Sonos system, Hue light hub, and LiftMaster garage door hub to name a few and never have had a single problem connecting with any of them.
At this point, rather than jack with my network that had a billion devices configured and connected to it, I set up a guest network on the same router and went with WPA encryption. This too was impossible to connect to though I made numerous attempts. I would’ve attempted the WEP encryption but that’s not an option on my router which is likely because that it’s well documented how to defeat that protocol and is not really considered secure anymore. After about an hour of fighting with it, I reluctantly set the guest network to an unsecured mode and it was only then that Guardzilla would connect to the network. Obviously, this is not an ideal situation for long term use as it leaves the network open for anyone to leech onto and even worse, potentially gain access to a device in the home that has a live video feed which ratchets up the creepy factor.
After putting Guardzilla through a week’s worth of use, I decided to futz with the network again and on the ASUS RT-AC68U router there is a setting called “B/G Protection” which was enabled on mine – likely by default. As I understand it, simplistically this keeps B and G devices from interfering with each other. Once I disabled this feature, Guardzilla was able to connect to my WPA-2 network just fine – and there was much rejoicing! I’m not sure why this particular device had a hangup with this but doing some net searching it appears that others have had similar issues with various devices so I can’t place any undue blame on Guardzilla.
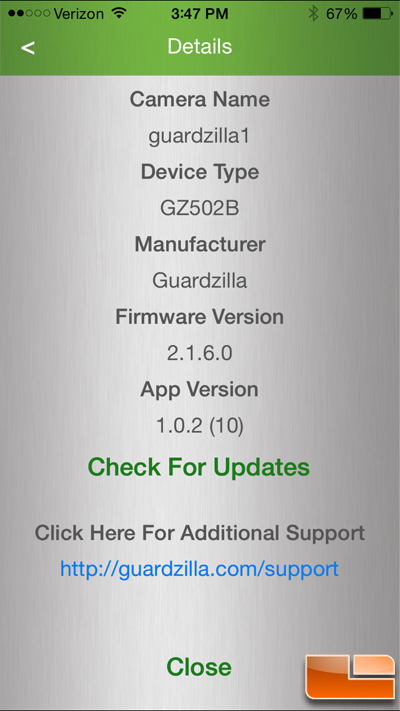
The firmware and app versions can be checked via the details screen in the app so if you are having issues, check here first for updates as it may remedy the problem. This is accessed by hitting the little blue encircled “i” icon on the app home screen.
