Mac Users Who Recently Installed HandBrake Pay Attention
If you are a Mac user and you recently installed the media encoding software HandBrake, you might have installed a backdoor onto your PC for hackers to take advantage of. ArsTechnica reports that hackers have compromised a server for the popular media encoding software and used that server to push out malware to Mac users.
The malware stole password keychains, password vaults, and might have stolen the master credentials needed to decrypt those passwords according to security researchers. The server dishing out the malware was compromised for four days ending on Saturday of last week. During that four day period the mirror at download.handbrake.fr was giving out a version of the software that was infected with the backdoor called Proton.
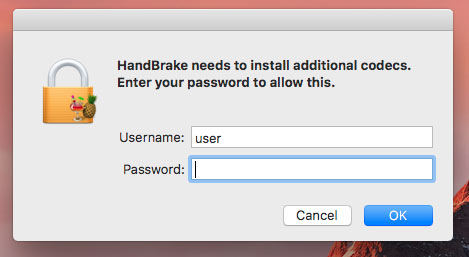
During the time the malware was distributed by the server none of the top 55 most common antivirus software platforms on the Mac recognized the backdoor according to Patrick Wardle, a security researcher. When the download was opened on the Mac systems the users were asked to enter their Mac admin password and that admin password was uploaded in plain text to a server controlled by the hackers.
User files were then sent to the same server when the malware was installed. If you downloaded HandBrake from May 2 to 6 you had a 50% chance of getting a malware laden installation since one of the two servers doling out the software was compromised. If you have HandBrake and downloaded it during that infected window and have a process called activity_agent running you are infected. Removing the infection is possible by removing the Launch Agent plist file fr.handbrake.activity_agent.plist and activity_agent.app file in the ~/Library/RenderFiles/. After removing this files reboot the machine and then change all your passwords.